
Mako Networks Central Management System - CMS
Mako Networks Security appliances are all connected to the Central Management System , whether you install;
- one Security Applicance for a small office like the Mako Networks 6500 or
- you have dual Mako Networks 7550 for a regional office in another county or
- a Mako Networks 8775 at Head Quarters as the firewall and VPN concentrator or
- you are managing a large number of retail outlets in a Petrol Station Chain throughout the county with 600 plus Secuity Appliances.

The Mako Networks Central Management System is the Magic that allows the reduction in cost, the ease of creating and changing
mesh networks, the ability to send a Mako Networks Security Applicance to a remote site and have its three cables connected ( Power, Internet/ADSL and LAN )
and start working almost immediately.
Mako Networks - Central Management System (CMS): MENU
- Home
- Provides a range of frequently used services
- Selection
- Lists the Mako Networks Applicances that are under CMS Management
- Reports
- Provides Usage, Status, Licences, Diagnostics and Syslogs for Mako's, PC's, Remote Access, Guardian and Sharknet IDS
- Configure
- ISP Setup, Alerts, IP Ranges, Networks, Firewalls, VPN's, Services like; QoS, Guardian, Failover, Dynamic DNS
- Management
- provides control for IT Services companies managing multiple customers Mako's including adding users
- Help/Docs
- Reference Library of PDF's to assist with configuring and managing different aspects of Mako Security Appliances
- Feedback
- Request for enhancements etc.
- Logout
Central Management System, CMS - Discussion
The following information on the Mako Networks Central Management System (CMS) is a discussion on some of the functions and features that are part of the
Mako Networks Security Appliance eco system. The CMS provides IT Services people and IT Network Professionals with Data, Tools and Reports to ensure that they
can manage the Security Appliance and and associated Network by providing information of the traffic passing through the firewall, the number of dropped connections and
the traffic going to each device on the LAN
Please note our discussion is only highlighting some of the functions and features, should you have queries or questions regarding Mako Networks Security
Appliances and the Central Management System CMS, then please contact IT Consulting & Services by email or phone and we can provide further information
and specific responses.
Email: sales@itcs.sg
Office: +65 6650 8750
The Menu System - Home Button
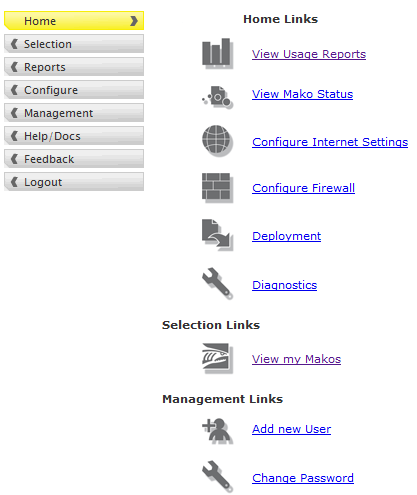
The Home Button provides access to the all the funtions available on the Mako Network Appliance. It provides some links on the home page to
areas that are normally required on a more frequent basis, like the Mako Status area and the Configure Firewall.
The Menu System - Selection Button
The Selection Button takes you to a list all the Mako Network Security appliances that are managed under your account on the Central Management System.
The list allows you to Select the Mako Networks Security Appliance that you need to work with to make changes, modifications and analyse the traffic through the
Security Appliance.
The Menu System - Reports Button
The Report system is extensive and placed next on the Menu system as it is more frequently used. All the traffic data is available and presented in an easy to
analyse layout, the Reporting allows for time based data to be selected and presented in bar graphs, pie charts and tabular data formats.
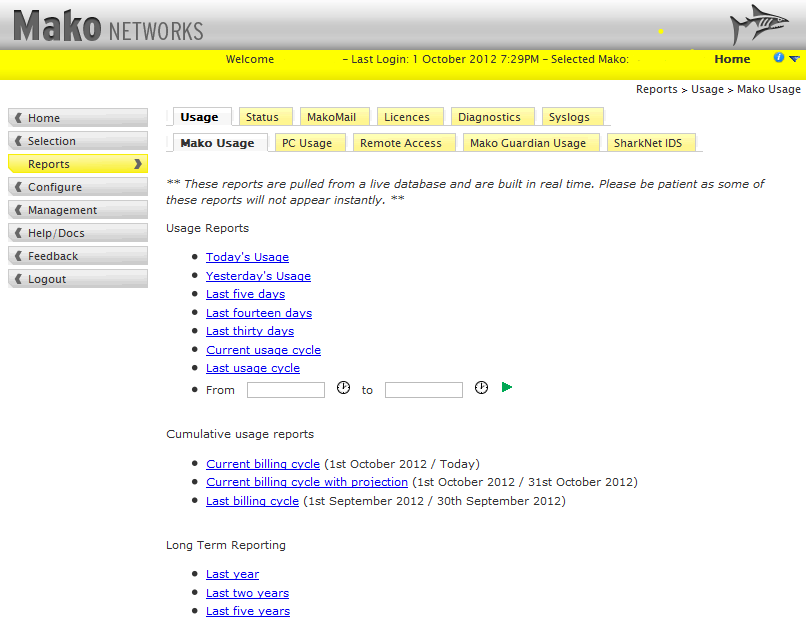
The available reports include Mako Usage, Status, Licences, Diagnostics, Syslogs, PC Usage, Remote Access, Mako Guardian Usage and SharkNet IDS.
Usage Report Screen - Showing the Mako Usage, Bar chart below for inbound traffic volume and outbound traffic volume. Within the screen there are links to
traffic by PC connected to the Mako Networks Security Applicance using the same data.
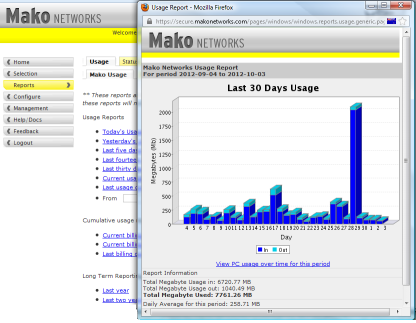
Similarly the presentation of the other types of reports are graphical using pie charts and tabular formats as appropriate
| Mako - PC Usage reports
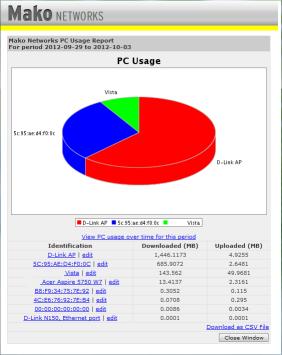
The network shown has a separate Wireless Access Point and a NAS box, these are listed on the pie chart. The tabular data identifies
other PC's that are not on the network when this image was created.
|
Mako - Sharknet IDS Reports

This pie chart is showing a significant number of intrusions from Singapore locations. There are also intrusions from countries like China and USA, but these are small in
number and lower down in the table not shown in this image.
|
| Mako - Firewall Log Report
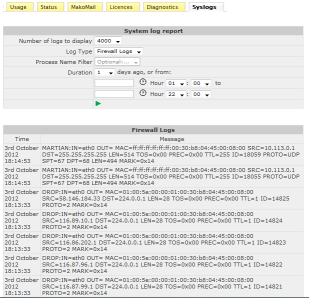
The Syslog report can be published by including the Firewall data or you can call up a separate firewall report as shown above.
|
Mako - Syslog Reports
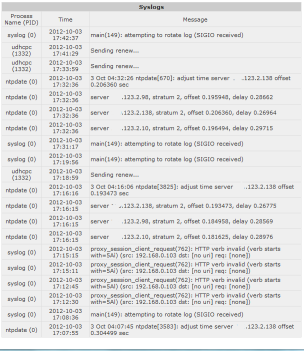
The Syslog reports are generated by selecting the date range that you require and then selection the number of records to be displayed.
|
The above reports are only a sample of the types of reporting that are available from the Mako networks CMS. There are several other tab's like the Mako Guardian
Usage, Licenses, Status and Remote Access that should you be interested then contact us and we will provide a presentation and demonstration of the Mako systems in
operation here in Singapore.
The Menu System - Configure Button
The Configure area is normally where you will start after a Mako Security Applicance has been installed on site. Within 15 minutes of being connected to the internet
the box will be available via the Mako Networks Central Management System - CMS. To have the Mako Networks Security Appliance connected you need to know all the
settings from the ISP. Mako Networks has contacted the ISP's and added the connection information to the CMS database and so you select by country, ISP and then
the plan.
The screen shot shows a drop down box with some of the telco operators that Mako Networks has installed in its database. Some of the plans for Malaysia are shown.
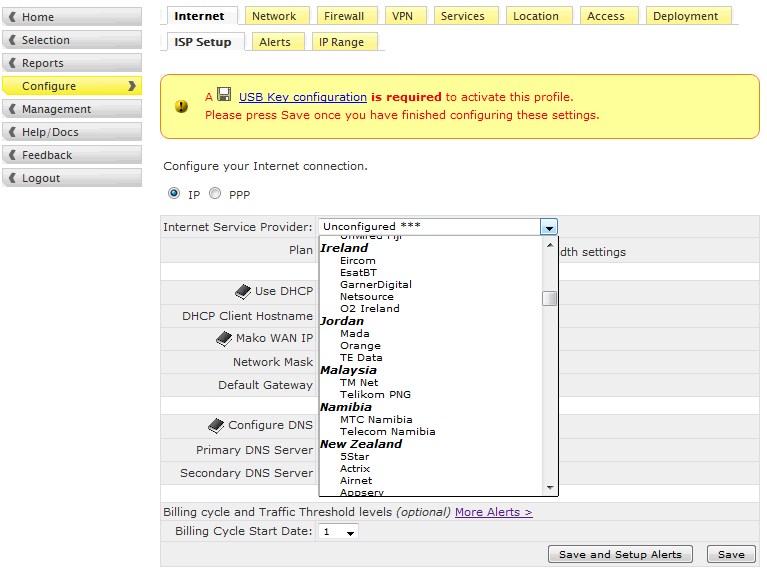
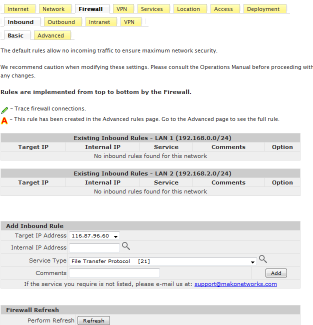
The screen shot shows the tabs under the Configure Button to connect to the ISP, set up the Firewall, set Alert messages by email or SMS. Important in this area are
the setup of the Security Appliance ports and the DHCP Servers by LAN port.
|
Mako - Configure Ports and DHCP Servers
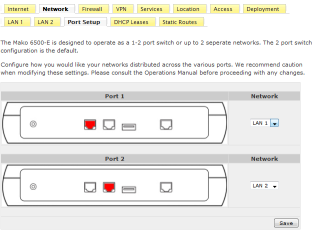
The Mako 6500 has been designed to operate with a different IP range and DHCP Server on each port - this provides the necessary separation when Payment
Card Industry Data Security Services - PCI DSS is implemented.
|
Mako - Configure Quality of Service(QoS) for Outbound traffic
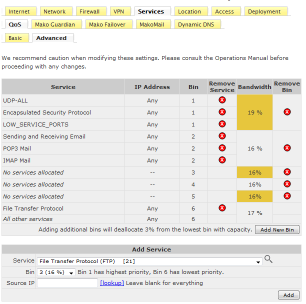
The Mako 6500 provides for QoS - management of outbound traffic. The settings are based on the bin concept and there is an allowance for
six bins. The bandwidth of each bin can vary until the traffic reaches 100%. Services not allocated to a Bin use the last bin by default
|
|
Mako - Configure Three Click VPN's
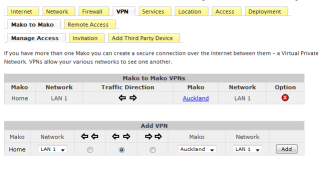
One of the foremost features of the Mako Secuity Applicance is the three Click VPN's - building a Mesh Network is simple, select the first Mako Security Appliance
from a drop down box, select the second Mako Security Appliance from a drop down box and then clicking to join them in a VPN.
|
Mako - Configure Firewall - Certified by ICSA Labs
The Mako Security Appliances Firewall has been certified by ICAS Labs and by
visiting the site you can verify by undertaking a search to find Mako Networks listing. Choose Mako Networks from the Certified Product Vendors list.

|
Mako - Configure Access Alerts
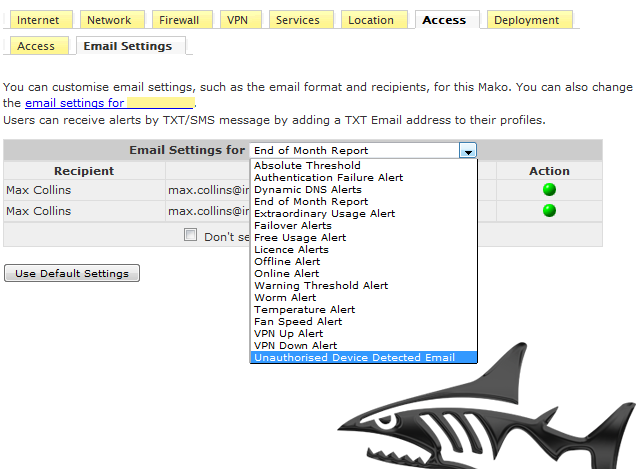
The Access Alert configure screen above Drop Down shows a list of Alerts that can be configured to be sent by email or SMS in the event of specified conditions.
The Menu System - Management Button
This location allows for Administration tasks relating to IT Systems Integrators that manage their clients Security Appliances, Users and Users Access rights.
The Menu System - Help / Doc's Button
Provides a list of Manuals and technical white papers in PDF format that users can down load at your convenience
The Menu System - Feedback Button
A text box is provided for suggestions, product features, CMS web site usability, support issues, information and data that you provide to Mako Networks.
The Menu System - Logout Button
The logout button, logs you out of the CMS system and you are exited to the login screen
The Mako Networks Security Appliance "Central Management System" - CMS was created and developed by Mako Networks
IT Consulting & Services in Singapore Sells and Supports Mako Network Products
Mako Networks and IT Consulting and Services entered into an agreement in September 2012 where IT Consulting and Services will sell and support Mako Network products
in Singapore. The Mako Networks range of Security Appliances also includes Network End Point gateways 6550 and Data Centre grade Internet gateways and larger
VPN Concentrators. Please refer to other pages on our site for the 6500, 7550 and 8875 models.
For further information on using Mako Networks Security Appliances, pricing information and proposals, Contact Sales at:
- Office: +65 6650 8750
- Mobile: +65 9780 2788
- ITCS eMail: Sales@itcs.sg
we would be delighted to help you.
|
Mako Networks range of Products and Services
Mako offers four Network Appliances, two of these the 6500-E and the 6500-A2 are targeted at small sites and businesses, the Mako 7550 is for larger sites
with additional capibilities as a Virtual Private Network Concentrator and as a High Throughput Gateway.
The Mako 8875 for the data centre and is designed for
high availability, a Virtual Private Network Concentrator and as a High Throughput Gateway.
Some of these applicances have more fucntionality
by adding additional licenses and all can be part of a Payment Card Industry Data Security Standard PCI-DSS certified systems to level 1.
Go to information on Mako Networks 6550-E and 6550-A2 Network Security
Appliance with 3G fail over
Go to information on Mako Networks 7550 Network Security
Appliance and VPN Concentrator
Go to information on Mako Networks 8875 Network Security
Appliance and VPN Concentrator
Go to information on
Mako Networks- CMS Central Management System
ITCS Industry Facts
Cyber-Crime in Singapore is a Goldmine
Firstly, some good news! According to Symantec, Singapore's number of viruses per computer is less than half the global rate.
While that is an impressive stat, it doesn't mean Singapore is free from cyber-crime. Far from it in fact. 72% of adults online in Singapore have been a
victim of cybercrime in their lifetime, 48% were in the past year. On average, the direct financial cost per victim is $657.According to Norton's 2012 Cybercrime
Report, that equates to more than 1.4 million people suffering approximately US$944 million in direct financial losses.
If that sounds like a lot, it's because it is. The global average is $197. Norton puts this down to greater affluence among Singaporeans and higher levels of credit
card fraud. Overall though, Singapore's cost of cybercrime is lower than other Asian countries; China lost $46 billion, while India's saw $8 billion losses. "Cybercriminals
are changing their tactics to target fast growing mobile platforms and social networks where consumers are less aware of security risks," said Effendy Ibrahim, internet
safety advocate and Director for Norton Asia.
"End users need to be made aware that virtualizing a business environment without implementing adequate security measures may be counterproductive, as it could
increase costs and reduce agility," said Frost & Sullivan, industry manager Cathy Huang
The Top 5 Risky behaviours with Mobile Phones
Mobile devices get smarter every day, and more of us than ever depend on them. But there is a drawback to our increasing dependence on
smart mobile devices—they have the potential to be even more risky than laptop computers. Matt Bancrof of Mformation quoting from a study
by the National Cyber Security Alliance list the following risly behaviours;
1. Disabling the lock feature on the phone and/or not establishing a password to unlock an idled phone
According to a survey commissioned by Pointsec, 85,000 mobile phones and 21,000 PDAs and smartphones were left on taxis in Chicago
over a 6-month period. The survey also found that more than 63,000 mobile phones and 5,800 PDAs and smartphones were left in London
taxis during the same 6-month period.
2. Keeping information that could compromise company security in "plain sight" on the phone
Companies surveyed reported that technical product, sales and/or customer details are being kept on employees' mobile devices, many
of which are personal devices rather than company-issued devices.
3. Opening an application from an unsecured/unknown source - like games!
In McAfee's 2008 Mobile Security Report, 64 percent of mobile Web users surveyed expressed worry about surfing on the mobile web/downloading content.
4. Using the phone to access dangerous/risky Web sites and Internet locations
One in seven global mobile users report that they have already been exposed to mobile viruses, either directly or through knowing someone whose phone has been infected.
5. Leaving the device open to access (e.g., leaving Bluetooth or WiFi on, visible and unsecured)
Some of the most prevalent mobile viruses and worms use an unprotected Bluetooth connection to get into mobile devices or to spread to other devices. This includes
two of the most common mobile device viruses, both with a number of variants, Cabir and CommWarrior.
DO SMBs need more Coffee, or Security
According to Dan Swinhoe of IDG 22% of SMB's spend more on coffee than they do on IT, That's a lot of companies.
Using data from the help desk people Spiceworks there are around 18 million SMB's worldwide with an average annual IT budeget of US$ 152,000. So by taking the average
budget and multiplying by 22% number is US$ 1,649,095,890.41 daily for the IT Budget.....
Now these companys are spending more that this number on Coffee....
However, the study said that one in six SMBs had suffered a security breach in 2011.
Mobility is popular among SMBs. iPads and other tablets were one of the main drivers of non-caffeine spending last year with 62%
already deploying, or planning to deploy the devices around the enterprise. The BYOD trend continues to grow, but security still remains
a grey area. Users and IT departments often clash in deciding who is actually responsible for device security, and almost three quarters
of SMBs do not agree that the use of mobile phones in business may represent a threat to IT security.
Elsewhere, the cloud is a set to be a big source of spending in the coming months and years. 48% of SMBs currently use the cloud, and
that figure is expected to rise to 62% by the end of the year, global spending totaling $40 billion. Spending and adoption figures are expected
to rise steeply in the coming years, reaching $100 billion by 2016.
According to Spiceworks, the largest portion of actual IT budgets (40%) is allocated to hardware purchases, with software (34%) and services (26%) following behind.
Most of the hardware money goes on desktops and laptops, while anti-virus and recovery top software choices.
So Dan conclude SME budgets seem to be increasing steadily year-on-year, and even if companies drank the world's most expensive coffee, at $80 a cup
$1.6 billion a year equals 20,613,698 cups, so no one is going to go thirsty.
Tablets - likely to surpass 350 million by 2016 - Mckinsey
Regionally, Europe along with Russia and Turkey are expected to constitute the largest market - accounting for one third of tablet demand - followed by North America
and Asia. The Middle East and Latin America will likely show the largest growth, representing around 50 million unites by 2016.
Five main factors will drive growth:-
1. affordability - low-end devices and natural price decline will provide access to less affluent customer segments, providing 60% of the growth.
2. replacement - many consumers will replace outdated tablets
3. substitution - Approximately 6% of the increase will be as alternatives to laptops
4. business adotion - estimated at 4%
5. education initiatives - estimated at 3%
Japanese Consumers
McKinsey reported that the Japanese consumer is changing dramatically - They are moving to the internet to buy more private labels and by 2015 are expected to be spending
US$ 50 Billion annually from a base of US$ 30 Billion today. The current overall retail growth for Japan's retail market is -1.3%. Domino's Pizza planned on taking 5% of orders online
however they are currently achieving 35% - beyond expectations.
In a recent article distributed on the internet, Riverbed Technology Ltd advised that the following five factors should be used in providing IT Infrastructure:
1. Distance doesn't matter. 2. Applications and data must bed everywhere - and in one place. 3.Knowledge must be harnessed - and data must be
managed. 4. Business never stops and 5. There are no second- class enterprise citizens.
Return to ITCS Home page
|
















